Authentication Solutions
Solutions overview
Fourthline’s Authentication solutions assess different factors to establish the identity of existing clients (whose identity we have previously verified) to access your services. Create different levels of authentication or step-up authentication flows.
Solutions include:
| Solution | Description |
|---|---|
| Client Authentication | Authenticate a client's identity using their biometrics and location. |
| Document Authentication | Authenticate a client's new ID document. |
Client Authentication
This solution assesses biometrics and location to establish the identity of an existing client, for example if:
- The client has a new device.
- The client forgot the password for or has otherwise lost access to an account containing funds.
- The client is performing a transaction from a high-risk geolocation for an amount over a specific threshold.
It includes:
| Product | Required |
|---|---|
| Biometric Authentication | |
| Location Authentication |
The flow is as follows:
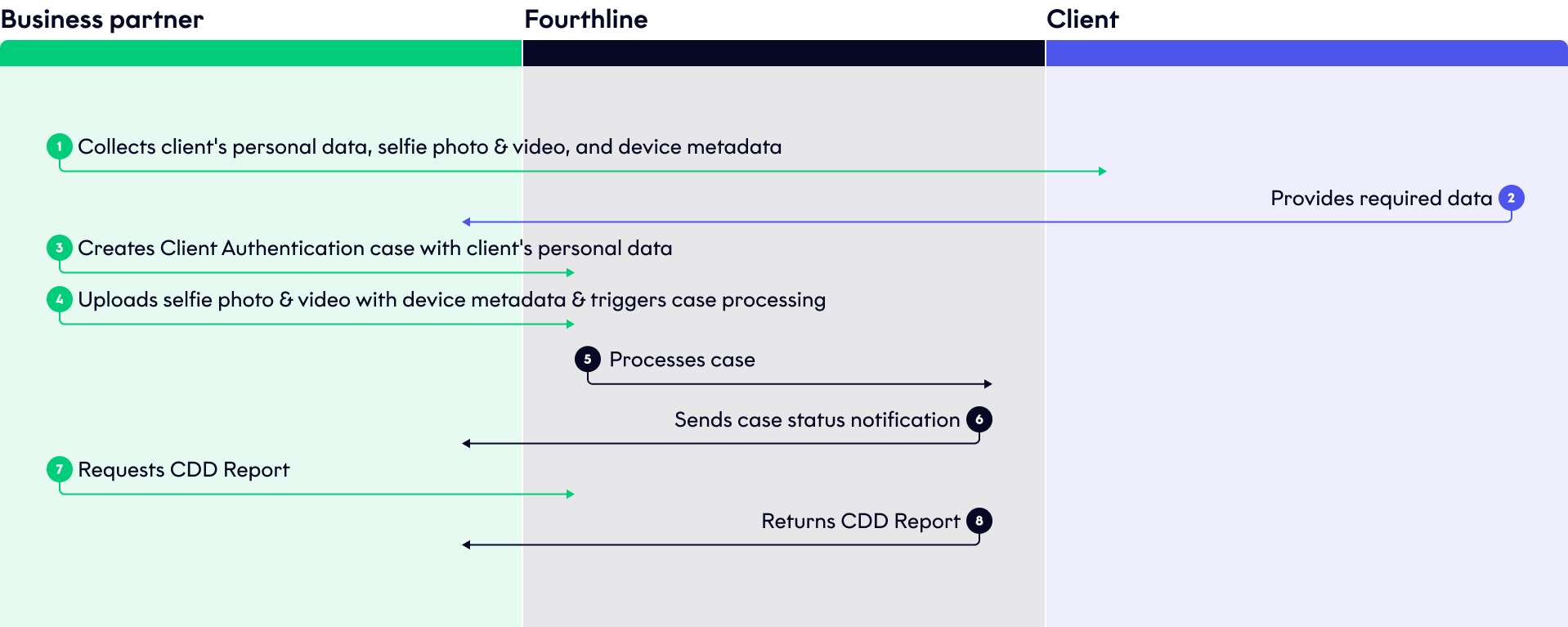

Biometric Authentication
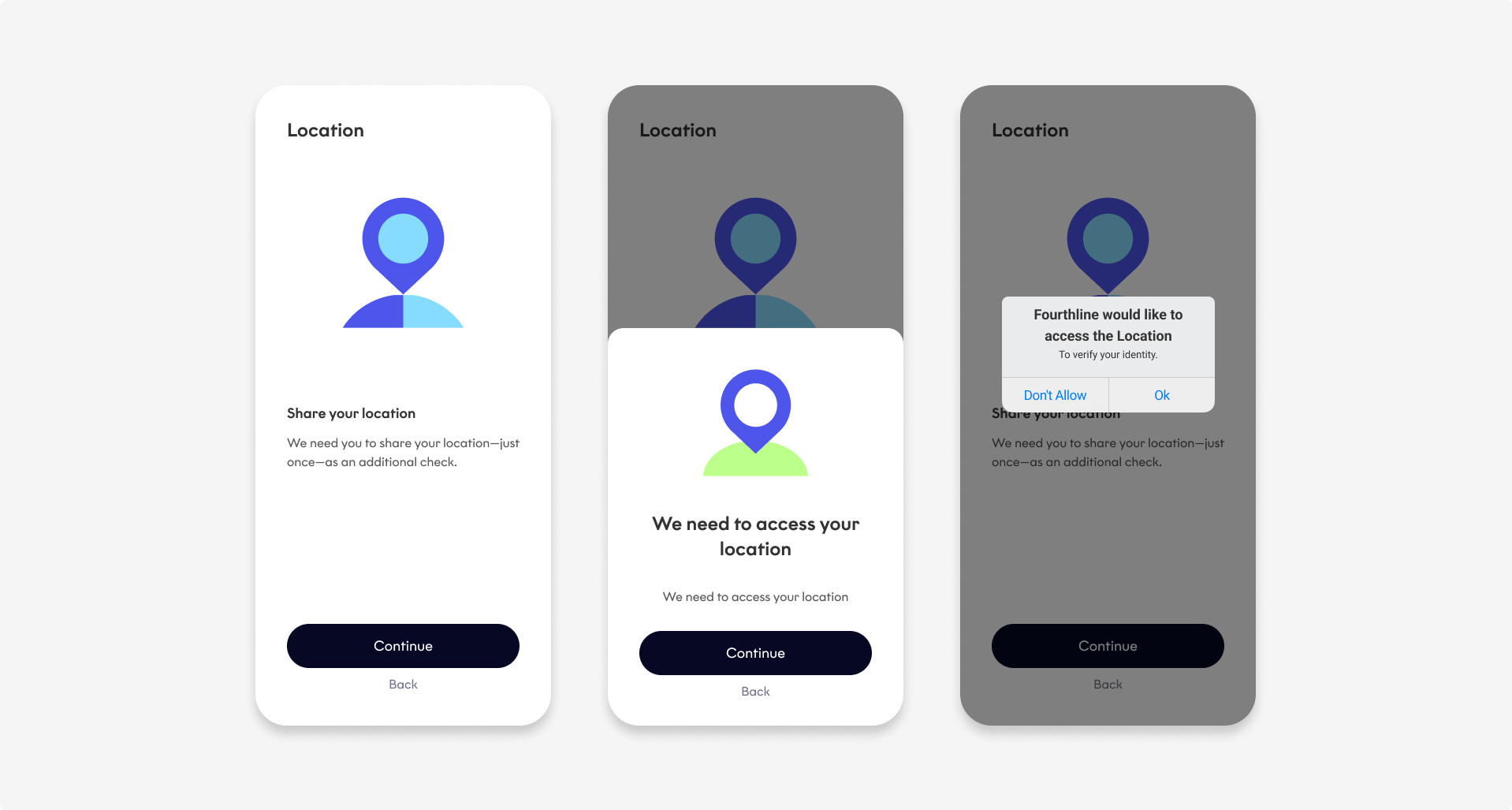
Location Authentication
When Fourthline has processed the case, download the detailed CDD Report via our API.
Document Authentication
This solution helps you ensure that existing clients have a valid ID document throughout their lifecycle. The client provides photos of their new document and we check that the document is fully visible, valid, authentic, supported, and in good condition with all security features present.
Fourthline compares the document data to their latest successful Identity Verification to confirm it belongs to that client.
It includes:
| Product | Required |
|---|---|
| Document Authentication | |
| Document Liveness | |
| Document NFC |
The flow is as follows:
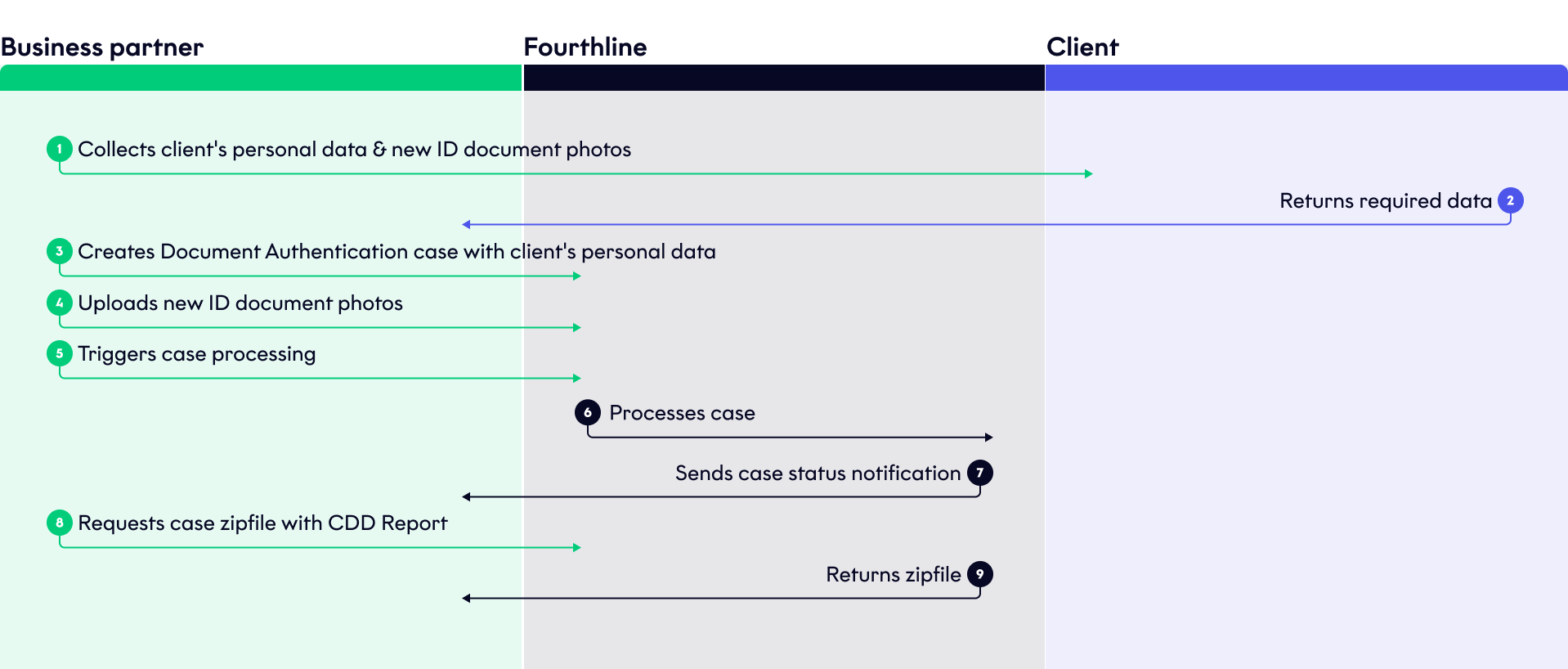
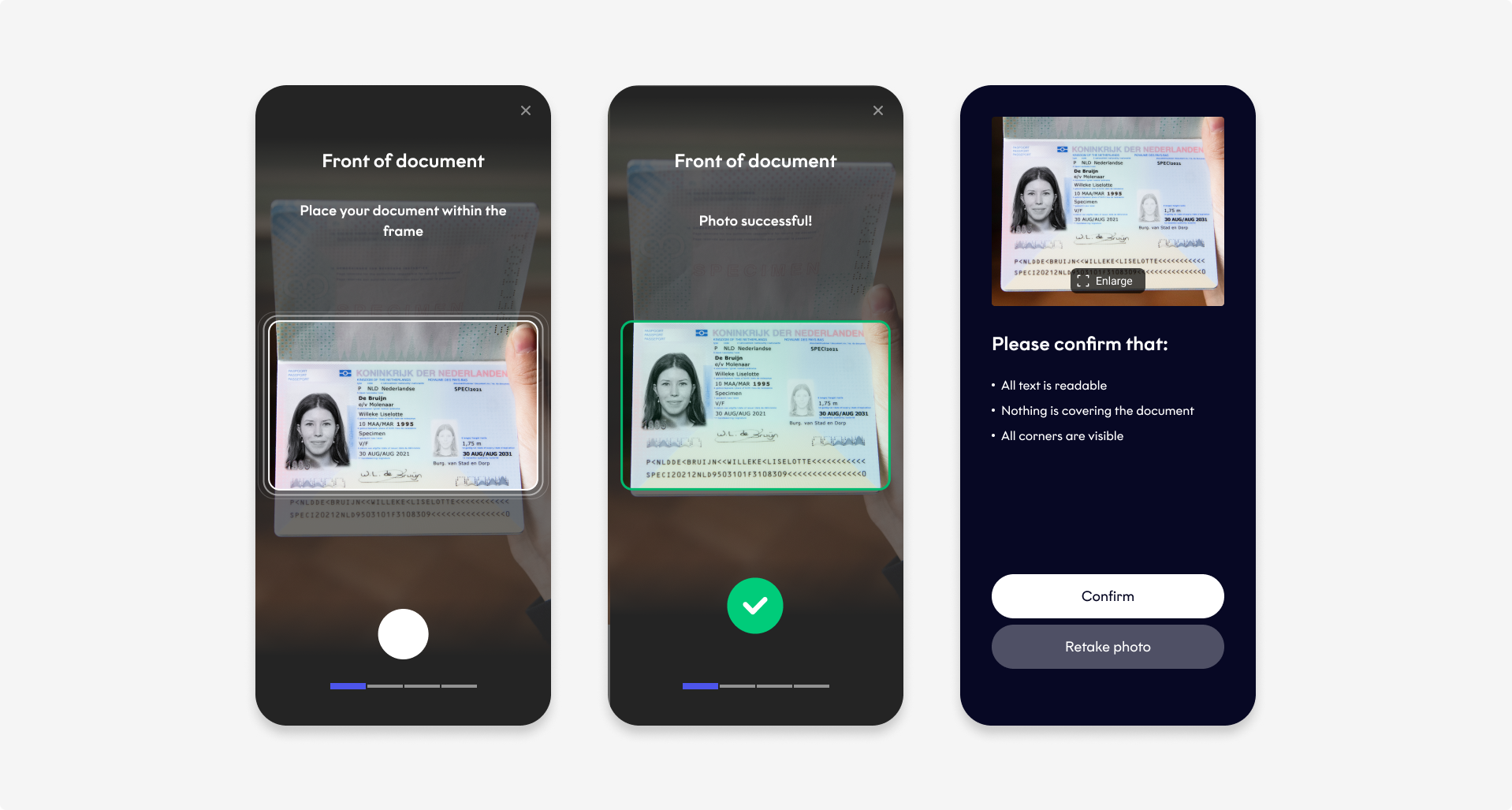
Document Authentication
When Fourthline has processed the case, download the detailed CDD Report via our API.
You can also draw on our extensive, specialist knowledge of KYC and AML compliance regulations within Europe and beyond.
Updated 4 months ago